FAQ
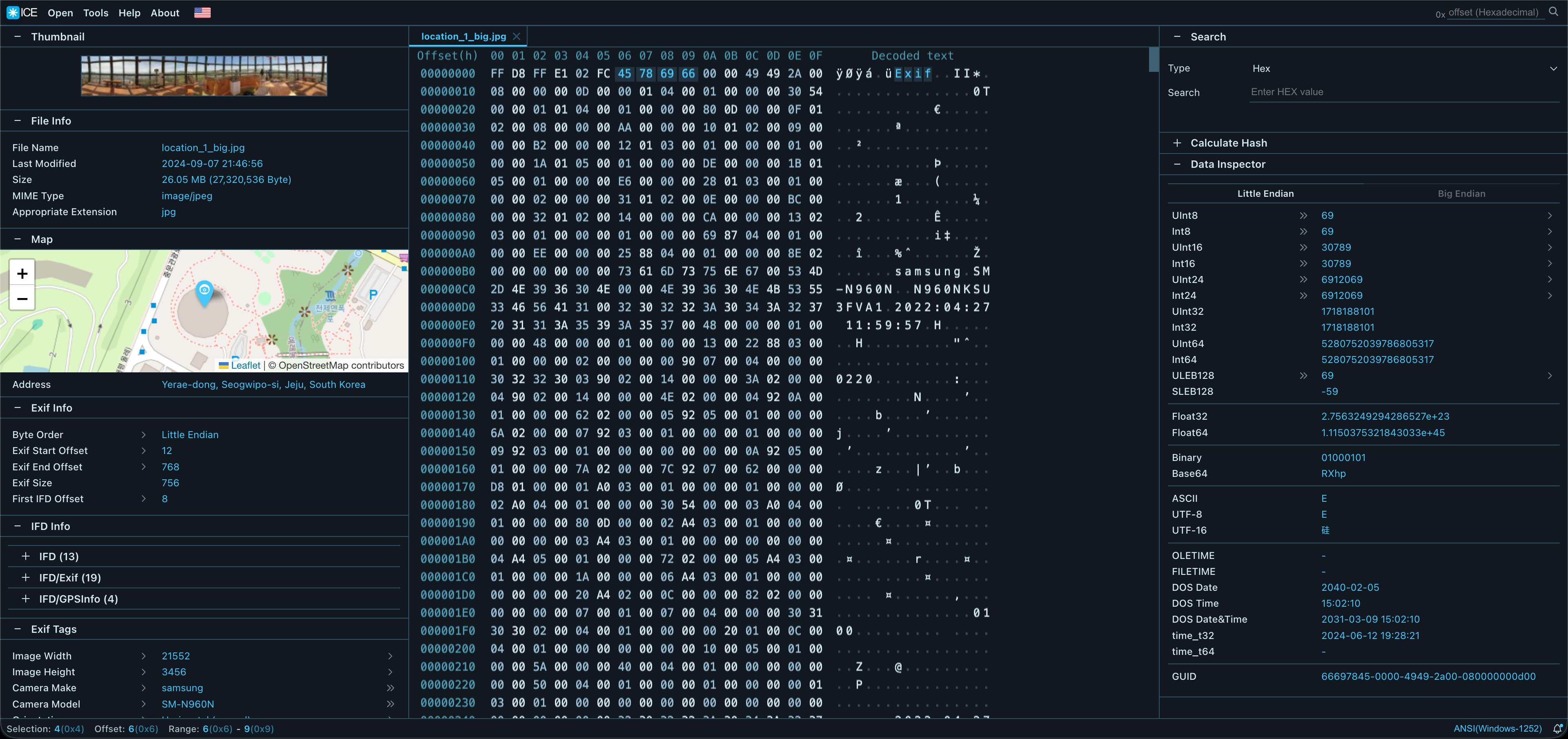
Q. What features are included in the Web-based Hex Viewer?
It visualizes raw binary data in hexadecimal format for deep inspection. Features include instant offset navigation and automatic data interpretation for types like UInt, Float, and Time, providing a professional forensic environment.
Q. Which file hash algorithms are supported?
We support all standard algorithms including MD5, SHA-1, SHA-256, and SHA-512 for verifying file identity and integrity. Large files are processed instantly via local WASM technology.
Q. Can it handle large images or binary files?
Yes. Utilizing WebAssembly (WASM) for efficient memory management, the tool can load and analyze files over several hundred MBs in real-time without browser freezing.
Q. Are my photos or analysis data stored on a server?
Absolutely not. This is a client-side tool where all analysis occurs on your device. Not a single byte is sent to an external server, ensuring maximum data privacy.
Q. Can it extract prompts from AI-generated images like Stable Diffusion or NovelAI?
Yes, with full support. It extracts hidden prompts, model details, and seeds embedded in iTXt or tEXt chunks. It perfectly interprets metadata from ComfyUI, WebUI, and more.
Q. Is it possible to check metadata for corrupted or broken images?
Yes. By using binary stream scanning instead of standard rendering, it can recover text information as long as the file header (IHDR) or metadata chunks are partially intact.
Q. Does it support screenshots from mobile devices like iPhone or Android?
Yes, it fully analyzes eXIf and standard PNG chunks within mobile screenshots, providing details such as device info, capture timestamps, and resolution.